This report is available in Uzbek and Russian.
Human Rights Defenders (HRDs) and journalists from Uzbekistan are under threat from a campaign of digital attacks, which has used phishing emails, Windows and Android spyware, a new Amnesty International investigation reveals.
A new report released today describes a campaign of malicious emails using fake websites along with Windows and Android spyware embedded in legitimate software. This campaign was active between May and August 2019 and targeted HRDs from Uzbekistan. The identity of the person or group behind these attacks is unknown, but this campaign fits into a larger pattern of digital attacks against Uzbekistani activists and journalists already reported by Amnesty International in 2017.
New Phishing Techniques
What is phishing?
Credentials phishing (or “Password-Stealing Phishing”) consists in the creation of a website that imitates the login prompt of a given online service, such as Gmail or Facebook, with the objective of luring a victim into visiting the malicious page and entering their username and passwords, thereby transmitting these credentials to the attackers.
Our investigation reveals that this attacker sent phishing emails in the form of fake Google or Mail.ru alerts with a link to a website that mimicked the same original websites. Amnesty International identified a partial list of people targeted by this attack and confirmed that several HRDs and journalists from Uzbekistan were among those targeted.
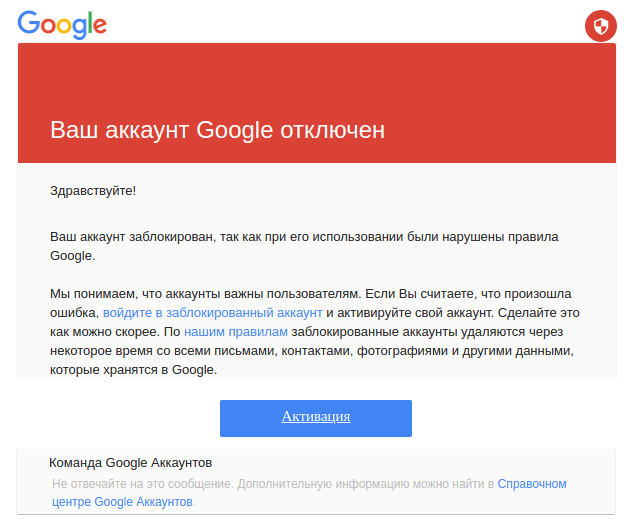
In previous campaigns, the attackers used cloned pages of legitimate websites in order to lure targets and steal credentials. Now, our latest report shows that the attacks have recently started to use a more advanced technique called “session hijacking”, consisting of a relay between the phishing site and the real affected website, in order to bypass most forms of two-factor authentication (2FA).
What is Two-Factor Authentication (2FA)?
Two-factor authentication (often called 2FA) refers to a second mean of authentication beside a password. Common second factors include a temporary code delivered by SMS, a temporary code given by a Smartphone Application (such as FreeOTP or Google Authenticator) and a code generated by a Hardware Security Key (like Yubikey or Solo Key).
It is the first time that we observe this technique used by attackers and it reinforces the recommendations that we made in our recent reports, including our previous report from December 2018 titled ‘When Best Practice Isn’t Good Enough’. In this report, we called for the adoption of stronger account protection measures, such as Security Keys, by HRDs.
Android and Windows Spyware
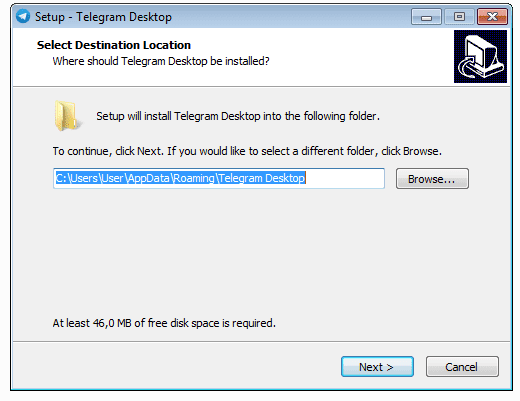
This investigation also shows that the attacker has developed Windows and Android spyware. The Windows spyware hides in a Telegram Desktop installer or Adobe Flash Player installer modified to install the spyware along with the legitimate software. Once installed it steals passwords, logs keystrokes and takes regular screenshots of the desktop.
The Android spyware is an evolution of an open-source tool called Droid-Watcher that was discontinued by its developer several years ago. It gives an attacker the ability to remotely monitor the compromised Android phone by recording phone calls, text messages and messages from chat applications such as Vkontakte, Telegram or WhatsApp. It can also extract the real-time geolocation of the phone.
Digital Security for Human Rights Defenders
This report is yet another instance of the growing threats HRDs face online. It highlights the predominance of credentials phishing as an attack tactic, and the attackers evolving ability to bypass common forms of two-factor authentication.
Amnesty International identified similar attacks in December 2018,. This latest report is a reminder of the growing pressures on HRDs when it comes to digital security. Today, the most reliable protection against credential phishing attacks are hardware security keys (such as Yubikey or Solo Keys).
If the email, or social media service you use does not support hardware security keys, other – although less reliable – forms of two-factor authentication are still useful basic precautions to at least thwart casual attackers and mitigate password reuse.
If you want to learn more about phishing and how to be protected against it, please refer to Security Without Borders’ Guide to Phishing.
Surveillance: A Consistent Risk for HRDs in Uzbekistan
Amnesty International has documented serious human rights violations, including pervasive torture by security forces and arbitrary detention, in Uzbekistan. Impunity for past abuses continues to prevail despite recent reforms of the criminal justice system and the closure of detention centers notorious for torture. While more independent media outlets have now been able to operate inside Uzbekistan, the rights to freedom of expression, association and peaceful assembly continue to be tightly regulated, and civil society activists face reprisals for their peaceful activities.
In a 2017 report called ‘We will find you, anywhere’, we described the impact of similar digital attacks against Uzbekistani activists and journalists, that put many of them at risk and in some cases forced them to leave the country.
This report documents that targeted surveillance remains a threat to HRDs in Uzbekistan. The UN Special Rapporteur on the right to Freedom of Expression, David Kaye, has called on states to impose an immediate moratorium on the export, sale, transfer, use or servicing of privately developed surveillance tools until rigorous human rights safeguards are put in place to regulate such practices. Amnesty supports this call. As the Special Rapporteur has noted, “It is insufficient to say that a comprehensive system for control and use of targeted surveillance technologies is broken. It hardly exists.”
If you believe you have been targeted with attacks similar to the ones described in this report, please contact us at:




